- Create custom rules that catch team-specific issues
- Upload existing style guides for automatic enforcement
- Configure repository-specific standards via
greptile.json - Verify rules are actually being applied
- Debug when rules don’t work as expected
Required Permissions
Understand who can configure custom standards:| Action | Owner | Admin | Member |
|---|---|---|---|
| View custom context | ✅ | ✅ | ✅ |
| Create/edit dashboard rules | ✅ | ✅ | ❌ |
| Delete dashboard rules | ✅ | ✅ | ❌ |
| Edit greptile.json | Anyone with repository write access | ||
| View suggested rules | ✅ | ✅ | ✅ |
| Approve suggested rules | ✅ | ✅ | ✅ |
| Delete organization | ✅ | ❌ | ❌ |
Permission issues are common. If you lose edit access, check with your organization Owner.
Configuration Methods
| Method | Best For | Version Control | Scope |
|---|---|---|---|
| Dashboard | Quick experiments, org-wide defaults | No | All repos or specific ones |
| greptile.json | Production standards | Yes | Repository-specific |
Method 1: Dashboard
The quickest way to add custom rules. Changes apply within 2-3 minutes to new PRs.Create Rules
Rules must be specific and measurable: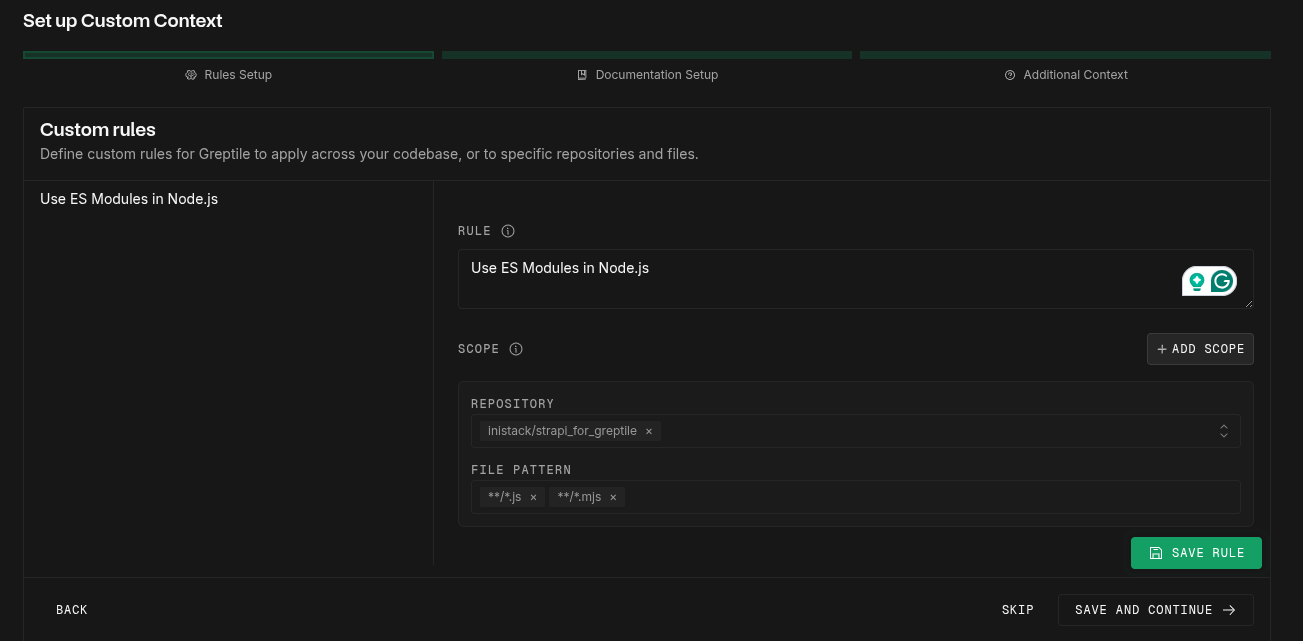
- ❌ “Write clean code”
- ✅ “Functions must not exceed 50 lines”
- ✅ “All API responses must include
statusandtimestampfields”

Upload Style Guides (Optional)
Point to existing documentation in your repository: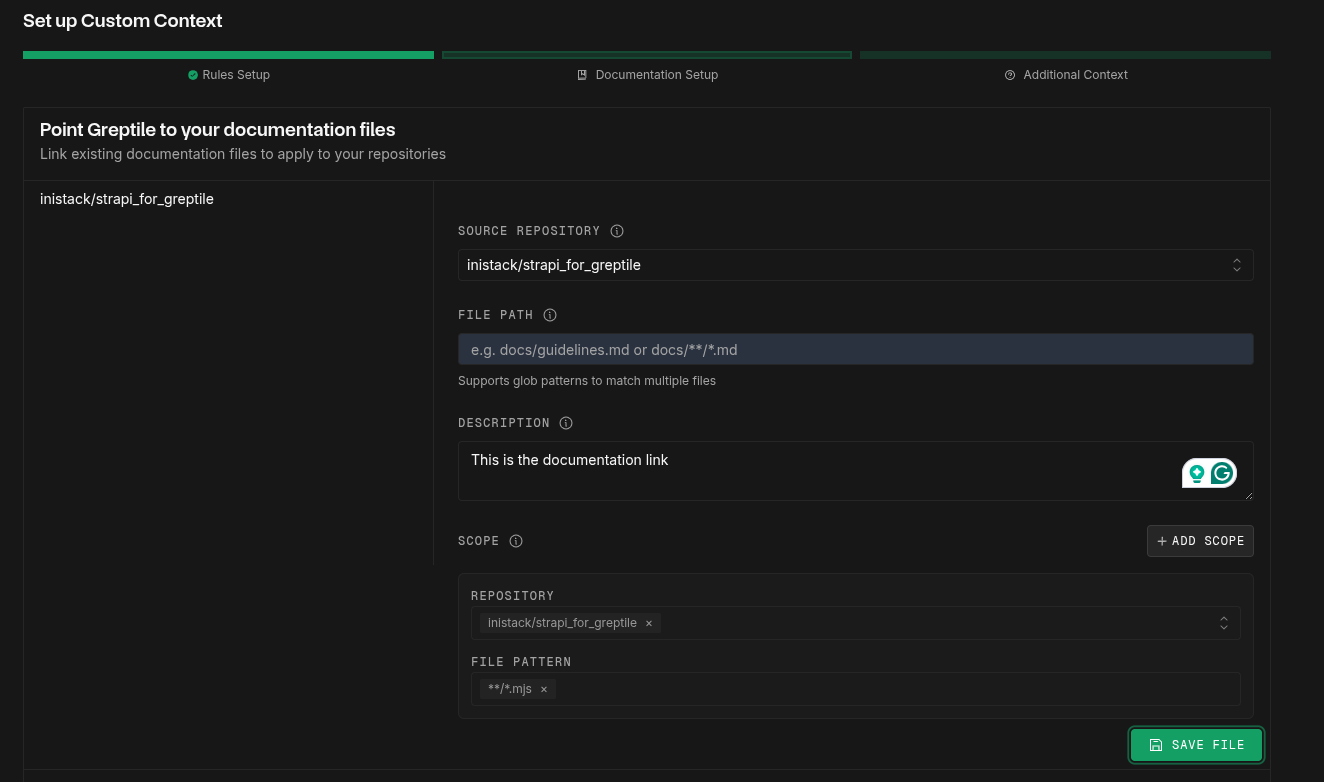

Method 2: greptile.json
The most powerful method - version-controlled, repository-specific configuration.Understanding customContext Types
ThecustomContext field in greptile.json accepts three arrays:
1. rules - Specific coding standards to enforce
files - Reference existing documentation
other - General context and background information
scope patterns using glob syntax to target specific files or directories. If no scope is specified, the context applies to all files.
Complete Configuration Examples
- Custom Rules
- Full Example
Verifying Rules Are Active
Many teams report rules “not working” - here’s how to verify:Check 'Last Applied' Status
Dashboard → Custom Context → Rules tab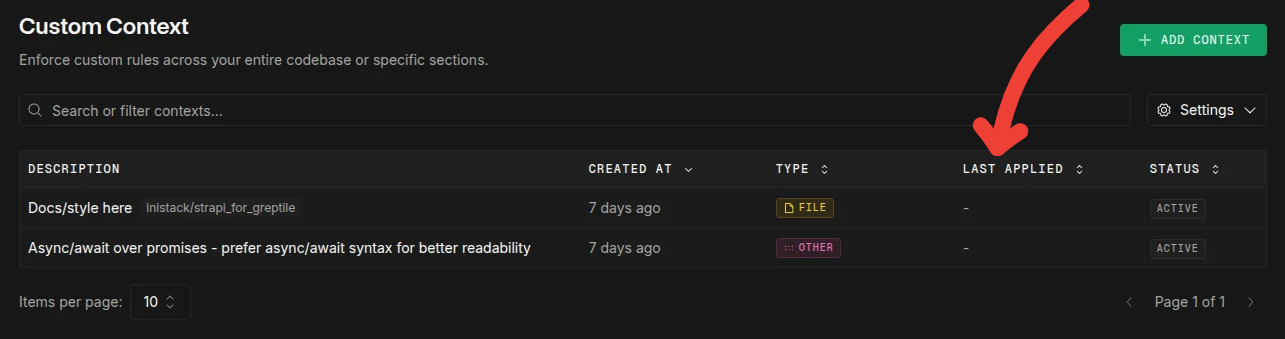

- Should update within 2-3 minutes of adding rule
- If stuck on “Never”, repository may not be indexed
- Force refresh: Create PR with
@greptileai review
Suggested Rules (Auto-Learning)
Greptile automatically suggests rules based on your team’s patterns: How it works:- After ~10 PRs, Greptile detects consistent patterns
- You can approve, modify, or ignore suggestions
- Duplicates may appear (safe to ignore)
Suggested rules may duplicate existing ones. This is a known issue - just mark as ignored.
Troubleshooting Custom Rules
Rules not being applied
Rules not being applied
-
Check “Last Applied” timestamp (Dashboard → Custom Context)
- If “Never”: Repository not indexed or rule not triggered
- If old: Rule may be inactive
-
Verify repository is indexed (Settings → Repositories)
- Status must be “Indexed” not “Indexing” or “Failed”
-
For greptile.json rules:
- Validate JSON syntax
- Rules won’t show in dashboard (this is expected)
- Takes effect on next PR only
-
Force trigger: Comment
@greptileai review this
Dashboard rules not syncing with greptile.json
Dashboard rules not syncing with greptile.json
This is expected behavior:
- Dashboard and greptile.json are separate systems
- greptile.json rules apply during review but don’t show in dashboard
- Dashboard rules don’t generate a greptile.json file
- Use one or the other per repository, not both
Pattern syntax errors
Pattern syntax errors
❌ Wrong - comma-separated string:✅ Correct - array of patterns:
ignorePatterns only affects reviews, NOT indexing. Files will still be indexed.Rules not specific enough
Rules not specific enough
Bad: “Follow best practices”Good: “Variable names must be camelCase, min 3 characters, no Hungarian notation”Include examples in your rule for best results:
What’s Next?
- Pattern Repositories → - Share rules across repositories
- greptile.json Reference → - Complete configuration options